Our services
Our services portfolio get your organization cover, from basic system monitoring to comprehensive Security Operations Center as a Service (SOCaaS) . By outsourcing security tasks to our experts, your business can focus on its core competencies, while maintaining a robust cybersecurity posture.
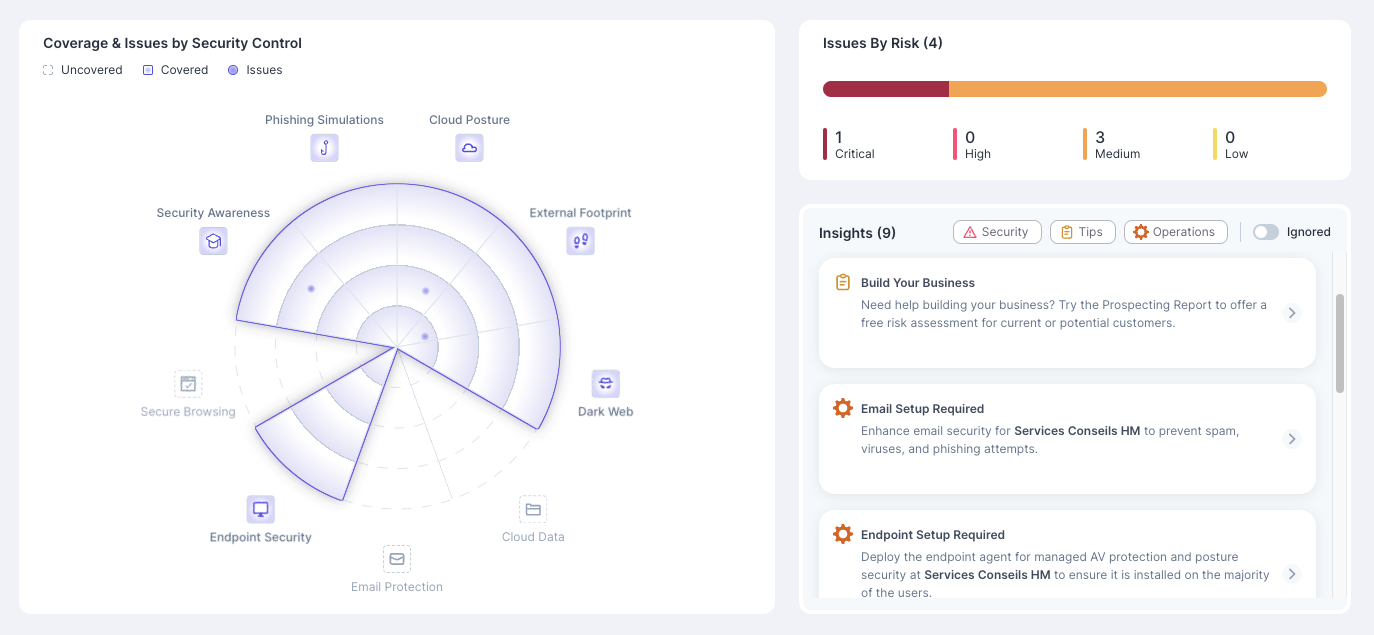
- Define existing security posture by assessing the overall strength of the organization’s cybersecurity framework.
- Conduct an asset inventory, including electronic assets, systems, and controls.
- Identify vulnerabilities and assess their impact.
- Define a strategic plan to adress vulnerabilities and enhance resilience.
- Information Technology Infrastructure
- Security-Related Policies and Practices
- Existing Protective Systems
- Compliance with Regulations
- Vulnerability to Security Incidents
- Resilience Against Harm
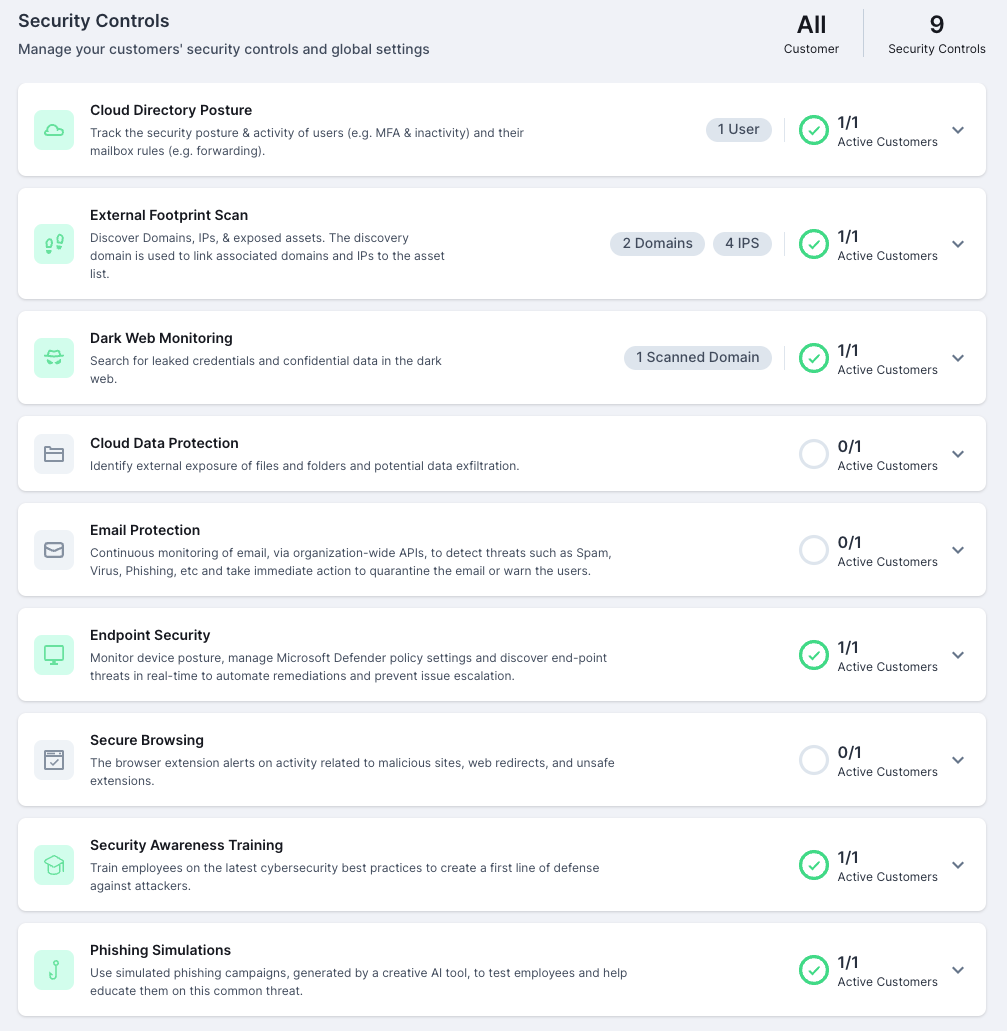
- Secure exposed digital assets with with Web Firewall that dectects and remediates vulnerabilities
- Prevent data loss by protecting IT infrastructure against data extrafiltration
- Keep browser secure from viruses and malicious sites with browser extensions
- Keep email secure by leveraging a user friendly API-based active protection service
- Enable cloud data protection to achieve a safe and secure data collaboration with external users
- Protect devices from cuber threats such as malware and ransomware
- Trackle insider threat and prevent corporate data leaks from critical devices
- Equip employees to the the first line of defense with our awareness training
- Simulate cyber attacks like email phishings to hightligh weak spots
- Dark Web monitoring : Getting one step ahead of cyber criminals can only be possible with monitoring them in the reconnaissance phase.
- Vulnerability Intelligence : Patching every vulnerabilities is impossible, but we are here to prioritize and keep your organization safe.
- Actionnable insights : Gain actionnable intel on external threats by scanning digital frootprint and exposed vulnerabilities
- Proactively prepare your enterprise against cyber threats rather than reacting.
- Take proactive actions in case of sensisitive data disclosure
- We employ cutting edge technologies to simplify and streamline the day-to-day work.
- Easy to inegrate with your current IT stack
- Our unified platform seamlessly detects, prevents, and responds to cyber threats in the most holistic, hassle-free, and cost effectie way.
- We provide technical support in case of security incidents, from mitigation to corrective measures
- Standard: Protection of external assets and including cyber threat intelligence service
- Premium: With the premium plan, you add internal asset monitoring
- All our packages include support for integration and incident response
- Monthly or annual subscription